It has been sometime to write about technologies, implementations and other things that interest me.
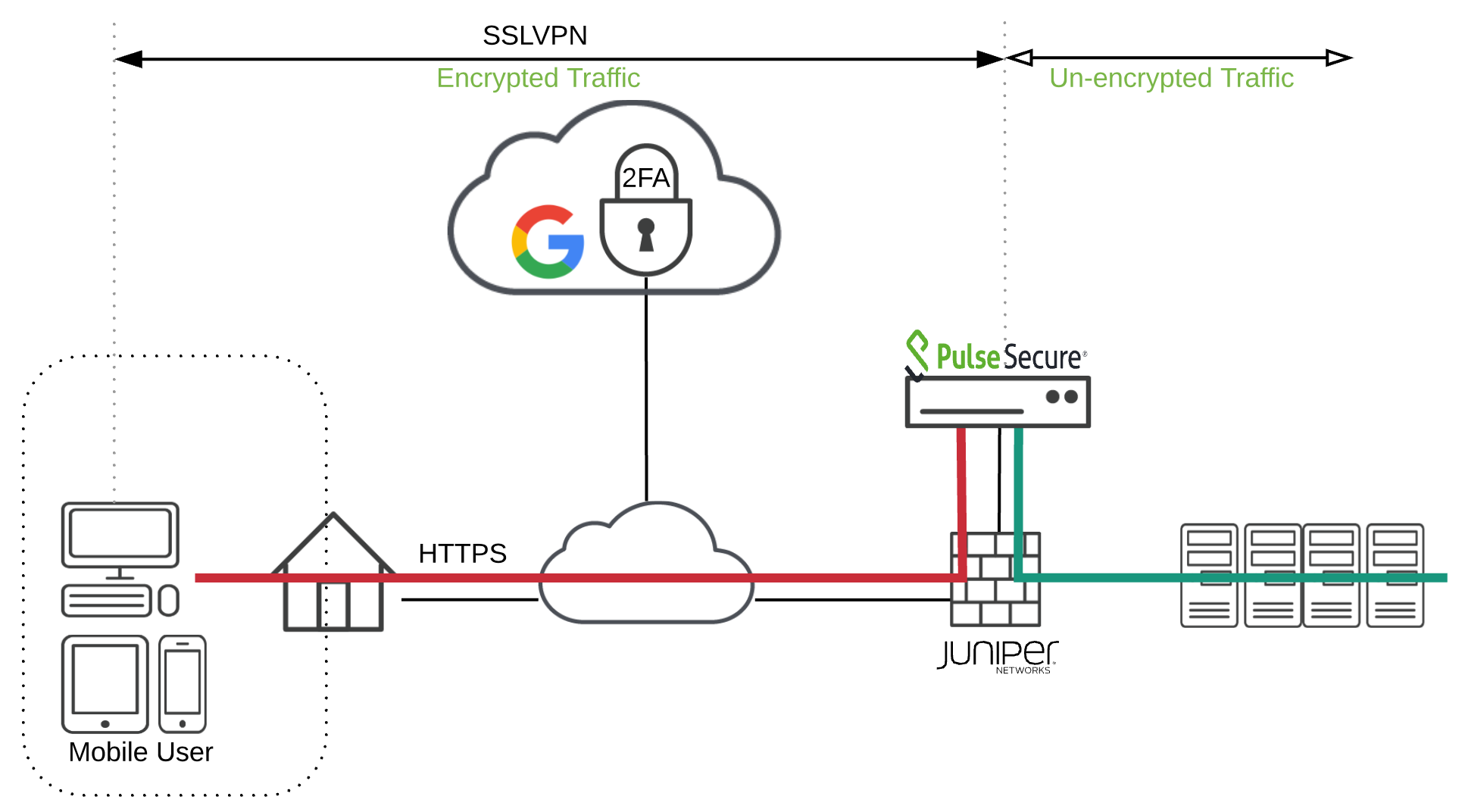
Today i found myself working again on SSLVPN and 2FA. Having previously worked with an SSLVPN and RSA, which was allways cumbersome to setup, i noticed there was an option to use google 2FA and decided to give it a try.
Products used:
- VMWARE – as a virtualisation methode
- Juniper SRX – as Perimiter Firewall
- Pulse Secure – as SSLVPN concentrator
- Google Authenticator – as 2FA means
Please note this will not go into detail on howto setup a firewall or sslvpn concentrator, mere on how you would integrate google 2FA onto an existing Pulse Secure device.
Step1: Logon to the Admin Page https://device/admin
Step2:
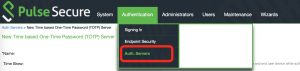
Step3:
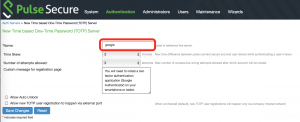
Step4:
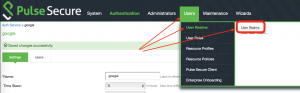
Step5:
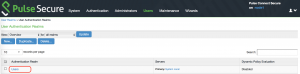
Step6:
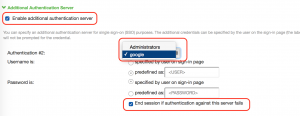
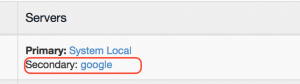
Step7:
Step8:
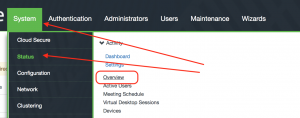
Step9:
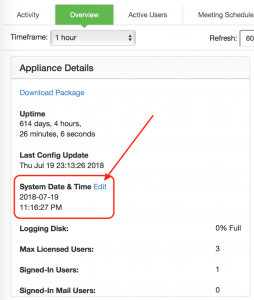
Step10:
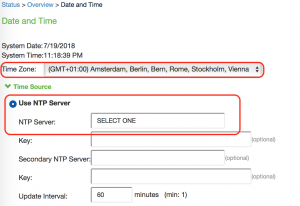
Pick a server from: NTP.ORG Server Pool
Step11: Download the mobile Google 2FA Authenticator from the app-sore or other trusted location
Step12: Login from LAN network the first time (for each user) to enable 2FA
Step13: Scan the QR-code on your mobile Google 2FA Authenticator
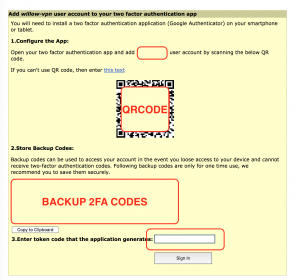
Step14: use the second generated code and enter this in the box on the page above.
Step15: Logout, 2FA is now enabled for this account.
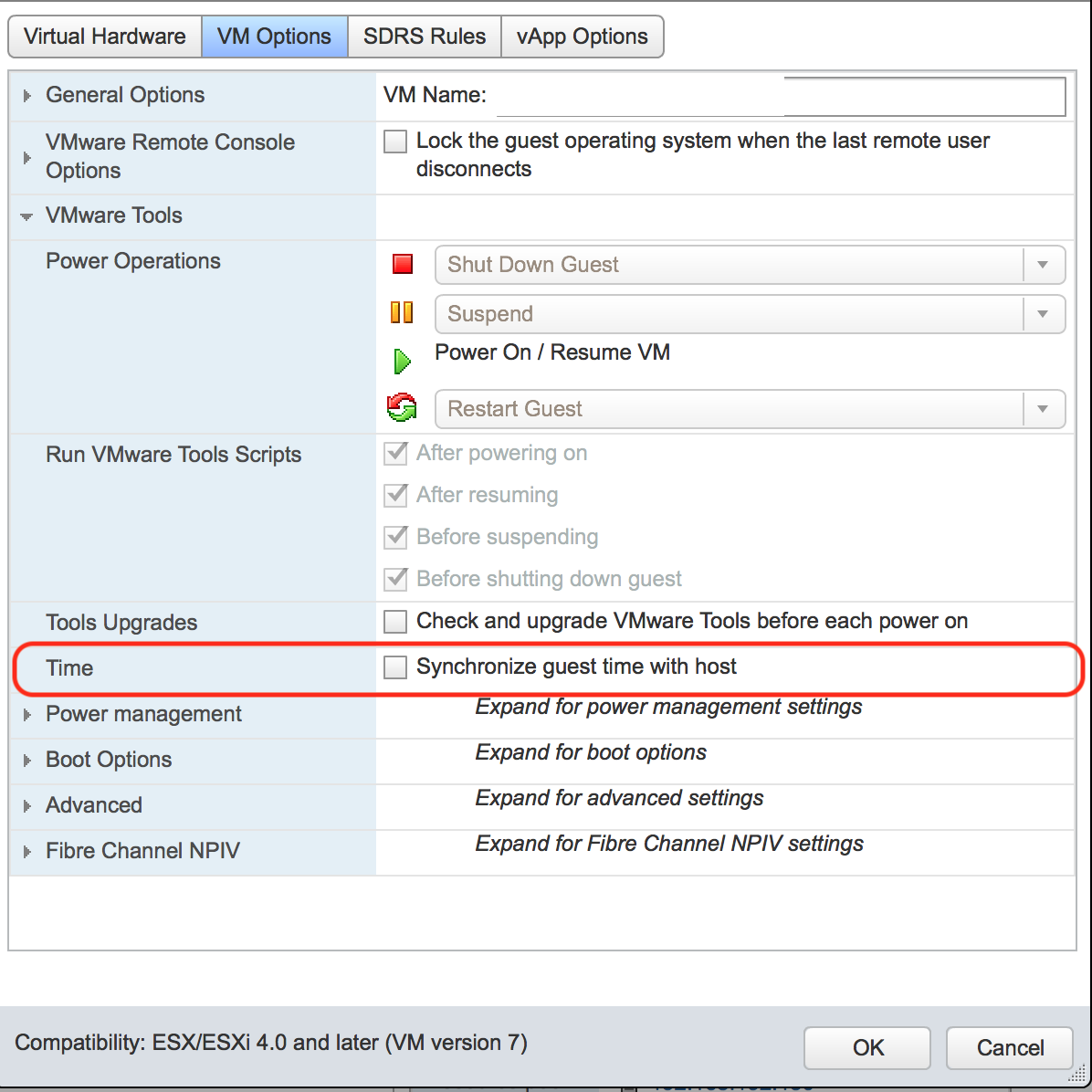
*** NOTE: when using vmware please make sure to uncheck: vmware:vmoptions->vmtools->synchronise guest time with host, and use a proper NTP server ***